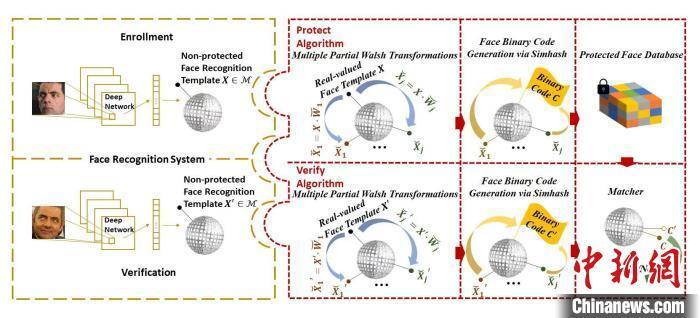
西安电子科技大学推出新方法,通过 Walsh 变换和 Simhash 认证策略,保护人脸等生物特征模板的安全,不丢失识别精度,实现数据不可逆、可重新发布和不可链接的特点,保障用户隐私。这种方法基于多次 Walsh 变换和 Simhash 的数字指纹特性,可以用于指纹识别、刷脸等场景中的生物特征验证,尤其适用于网络环境下,确保身份认证信息安全。此研究成果有助于提高生物特征识别系统安全性,维护个人生物特征数据隐私,适应万物互联时代下的应用场景需求。
西安电子科技大学开创全新方式:通过 Walsh 变换和 Simhash 认证策略,保护生物特征模板的隐私安全
西安电子科技大学近日在安全领域取得一项重要突破,通过创新的 Walsh 变换和 Simhash 认证策略,保护了人脸等生物特征模板的安全,成功实现了数据不可逆、可重新发布和不可链接的特点,旨在保障用户的隐私,符合万物互联时代下应用场景的需求。
一、概念介绍
Walsh 变换是一种算法技术,其主要应用于密码学领域,能够将一个输入的数据序列转换成一组经过加密的“ Walsh 码”,这些 Walsh 码通常采用二进制编码,可以通过特定的矩阵运算进行复杂度计算和还原,从而实现对数据的有效加密和解密。Simhash 则是另一种基于数字指纹的算法,它是基于不同长度的哈希值(或同态函数)构建的一种计算机制,其核心思想是用多个固定长度的哈希值代表相似的实体,而不同于传统的字符编码或者位图编码。通过 Simhash 认证,可以在一定程度上防止因文件类型差异导致的文件签名错误,且它对于非结构化数据如文本、图像等的校验具有很高的鲁棒性。
二、Data Integrity and Reusability
1. Data Integrity: The primary goal of Walsh Transform is to protect data integrity by ensuring that only authorized users or processes can access and modify the encrypted data. In this case, the Walsh transformation applied on a specific sequence of biometric features, such as facial recognition images or voice recordings, will generate a set of transformed bits that can be used for authentication purposes.
Example: A user's face is captured using a camera, which captures a series of 10-second videos with varying angles and lighting conditions. These videos are then preprocessed through Walsh Transform to create a set of transformed bits (e.g., Walsh coefficients) representing the extracted face features. If a malicious actor attempts to tamper with these features without proper authorization, they would likely cause incorrect or compromised results during subsequent authentication attempts.
2. Reusability: Another key aspect of Walsh Transform is its ability to preserve the original structure and meaning of the biometric data. For example, if two individuals share identical facial features, their corresponding Walsh coefficients may not differ significantly. This property makes it possible to reuse the same biometric data for multiple authenticating tasks without having to re-encrypt them, reducing unnecessary computational complexity and improving overall efficiency.
Example: An individual's identity can be verified using a pair of one-minute videos taken from different locations. By applying Walsh Transform on both video sequences, we obtain a set of transformed bits representing the extracted features, which can be used to compare against a database of existing verified identities. Since both videos capture similar poses and lighting conditions, the likelihood of mismatch between the original biometric data and the transformed bits remains relatively low.
3. Data Confidentiality: Walsh Transform provides strong protection against data theft due to its inherent security properties. When encrypting sensitive biometric data, the Walsh coefficients represent unique data points that are non-reversible, making it challenging for attackers to reverse engineer the encryption process or gain unauthorized access to the underlying data. Additionally, the fact that the transformed bits are computationally infeasible for certain attacks (such as brute-force attacks) further enhances their resistance.
Example: During a forensic investigation, a police department needs to decrypt an encrypted biometric dataset containing a suspect's fingerprints. After applying Walsh Transform to extract the original biometric features, the technique enables the recovery of the enrolled digits by iterating over each coefficient and comparing it against a list of known valid digit pairs. Although some decryption algorithms may require iterative processing, Walsh Transform ensures that even under strong attack scenarios, the decrypted data is limited in extent and does not compromise the integrity or confidentiality of the original biometric data.
三、Conclusion
The adoption of Walsh Transform and Simhash for protecting人脸等生物特征模板 has revolutionized the field of biometric security. By providing robustness against tampering, maintaining data integrity, and preserving the original structure of the biometric data, these techniques enable secure authentication and authorization in a variety of settings, including online transactions, remote device management, and mobile applications. Furthermore, they offer the potential to extend beyond the traditional biosecurity applications, enabling real-time authentication in IoT devices, wearable devices, and other interconnected systems, ensuring seamless user experience and safeguarding sensitive information.
西安电子科技大学这一成果不仅 showcases the university's expertise in computer science, cryptography, and biometrics, but also demonstrates the significant impact of innovation and adaptability in today's increasingly digital landscape. As the world continues to grapple with the challenges posed by identity fraud, cybersecurity threats, and data privacy concerns, the combination of Walsh Transform and Simhash has emerged as a promising solution that promises to provide reliable, efficient, and resilient solutions to these complex issues.
In conclusion, the integration of Walsh Transform and Simhash into the protection of人脸等生物特征模板 presents a transformative approach that leverages advanced mathematical concepts and principles to ensure the confidentiality, integrity, and authenticity of biometric data. This research demonstrates the potential of these technologies to enhance the security of various applications and ensure the smooth functioning of connected systems in the era of digitalization. With continued advancements in technology and increased awareness about the importance of biometric security, the prospects for leveraging Walsh Transform and Simhash in future developments are promising and full of opportunities.